Table of contents
- Here we'll work with minikube.
- Starting the cluster.
- Check the cluter info. Running at port 8443.
- Check nodes inside cluster. Here we can see the minikube node running.
- Using monokle to create manifests.
- Making sure everything is works fine!
- Kubescape oh my!!
- Reviewing the issues.
- In the local terminal.
- In the armo portal.
- Creating custom framework for the cluster.
- Rest of the things
- Personal Abstract
- Have anything to add?
Did you worked hard on maintaining and deploying your kubernetes cluster?If yes what about securing it?
Kubernetes uses a flat network model that allows each pod to communicate with any other pod in the cluster by default. This creates major security concerns, because it allows attackers who compromise one pod to freely communicate with all other resources in the cluster.
Yes. Kubescape by Armo helps you in securing your k8's cluster using the CUI as well as GUI.
To start. Let's see the prequisites.
- Firstly basic understanding of kubernetes. See the docs
Secondly we need a k8's cluster. Below you can see some tools to create a k8s cluster locally Minikube, Kind
Monokle, a friendly desktop UI for managing k8s manifests. We'll use it for creating yaml file for pods and replicas.
- Lens, a kubernetes IDE for visual representation of the k8's cluster.
- RBAC (optional)
- Whenever there is a term present in the kubescape, we italicize it.
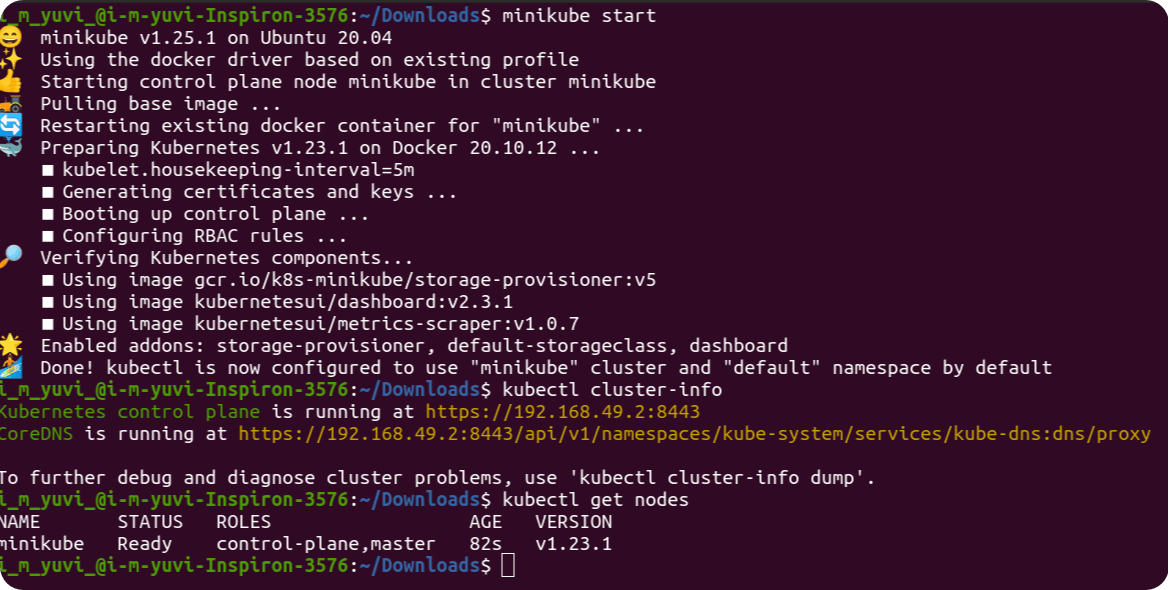
Here we'll work with minikube.
Starting the cluster.
minikube start
Check the cluter info. Running at port 8443.
kubectl cluster-info
Check nodes inside cluster. Here we can see the minikube node running.
kubectl get nodes
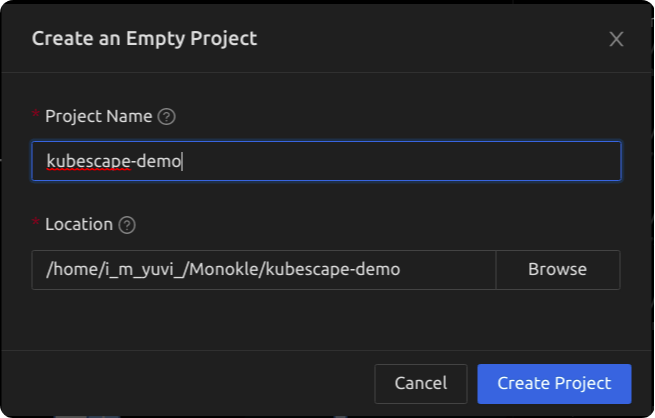
Using monokle to create manifests.
Create a project in monokle. eg. kubescape-demo
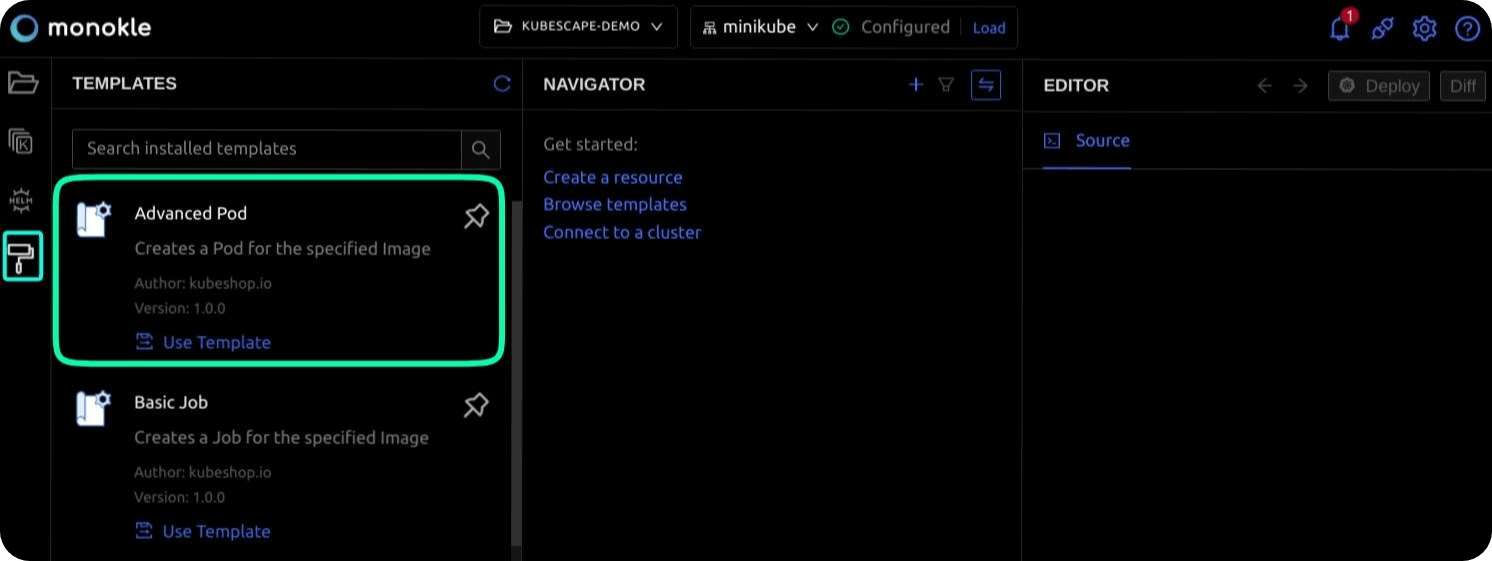
Create a pod manifests using the advanced pod template plugin. eg. name: demo-pod image: nginx namespace: default and deploy it to your minikube cluster.
Note: Since its beginning we don't require the command and args tags.
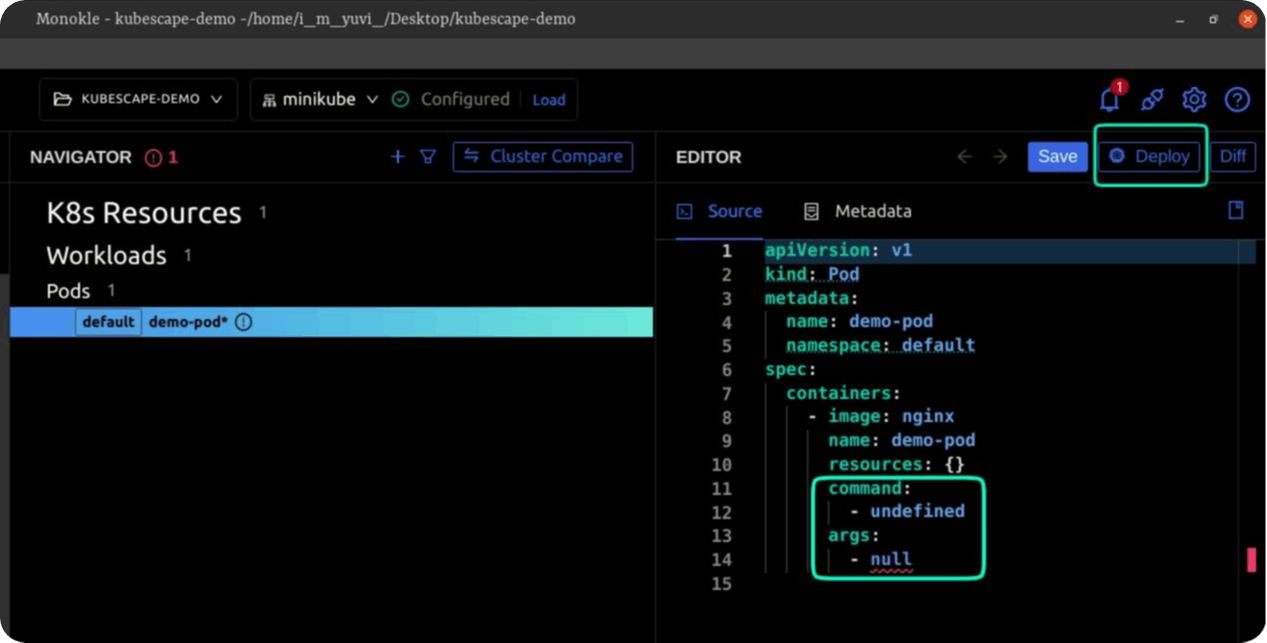
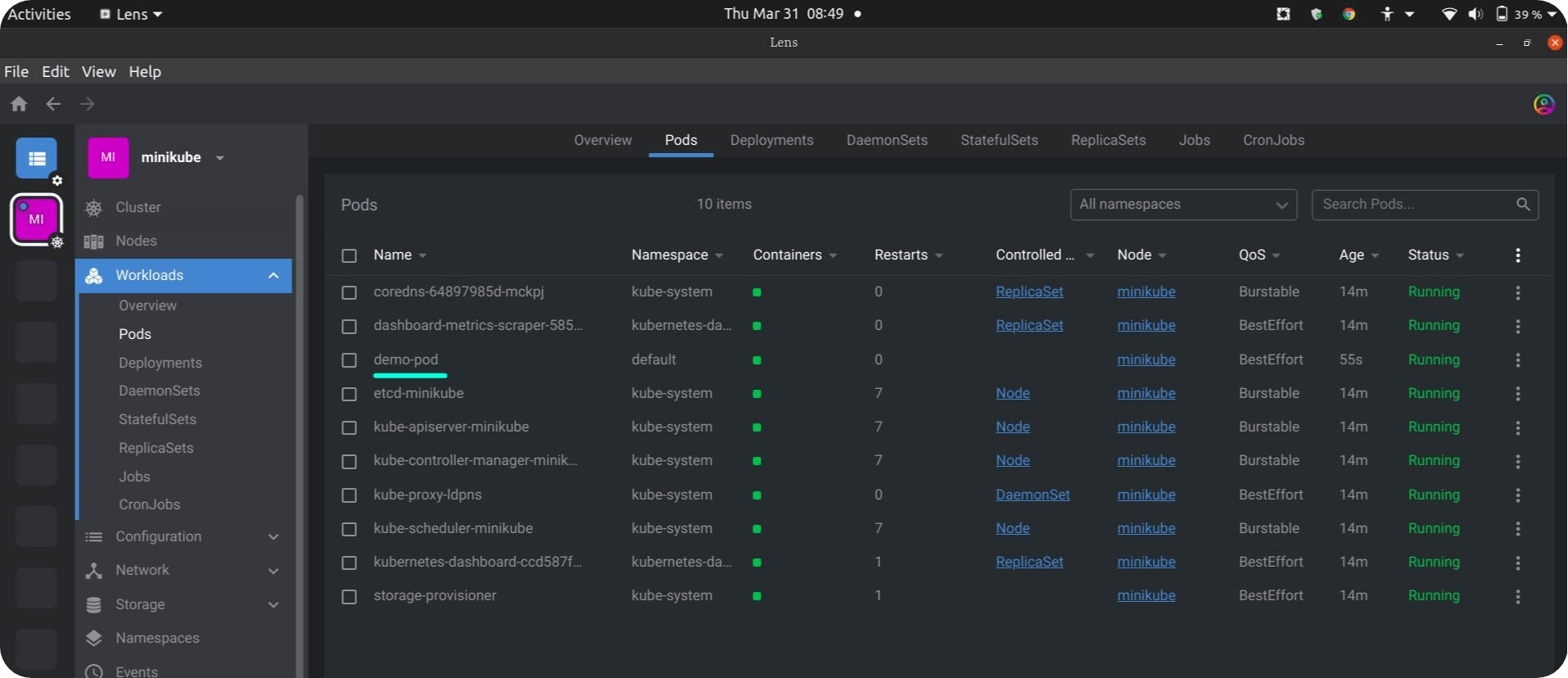
Making sure everything is works fine!
Using lens to see the minikube cluster and recently created the demo-pod.
Kubescape oh my!!
Make sure you sign up the kubescape and log into the portral. There in the Kubescape CLI – CI/CD Deployment section you will see the commands for installing and integrating your account into the local terminal.
kubescape scan --submit --account=<account key>
This will integrate your local cli with the armo cloud portal and run the scanning.
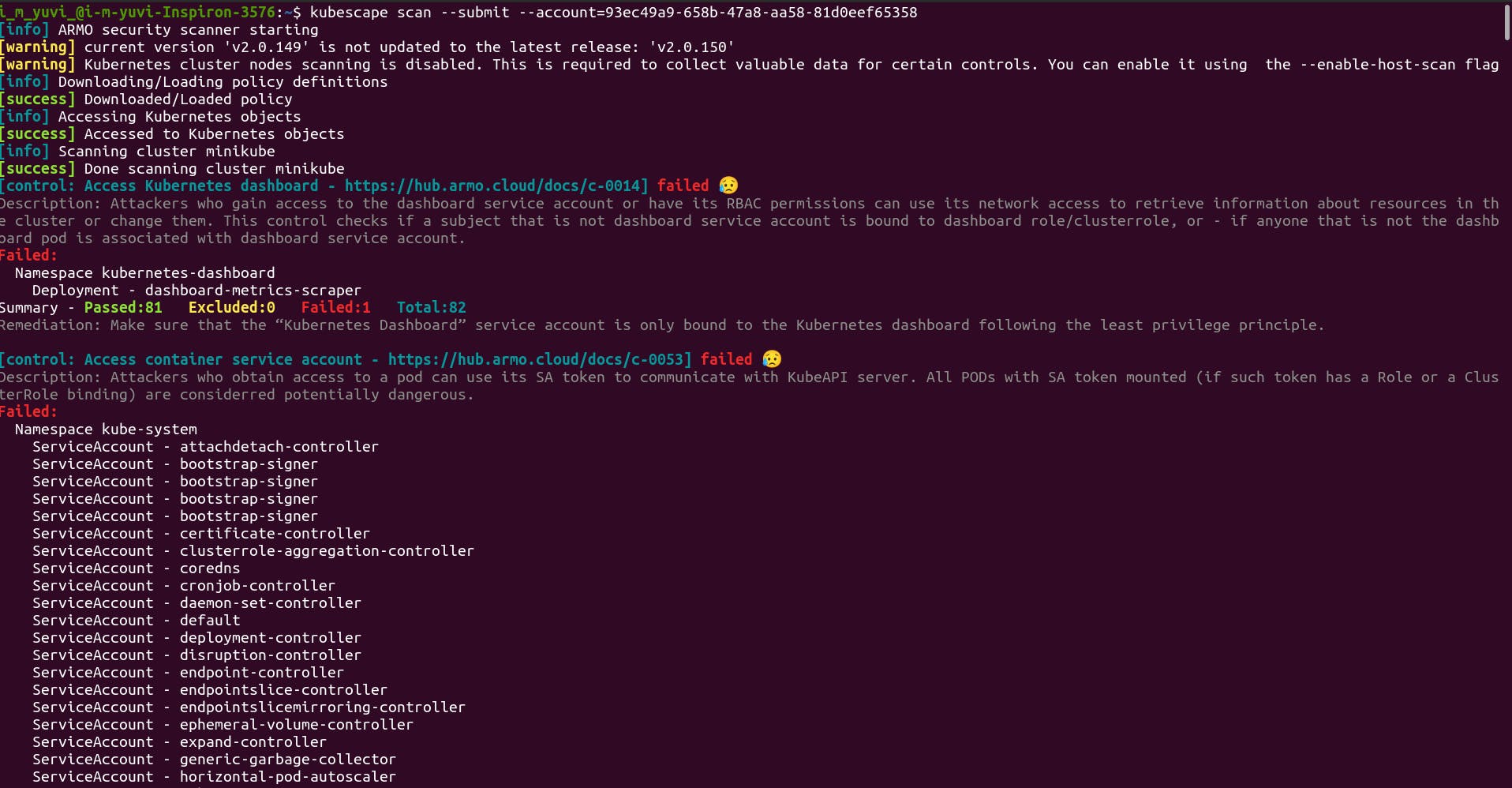
Reviewing the issues.
In the local terminal.
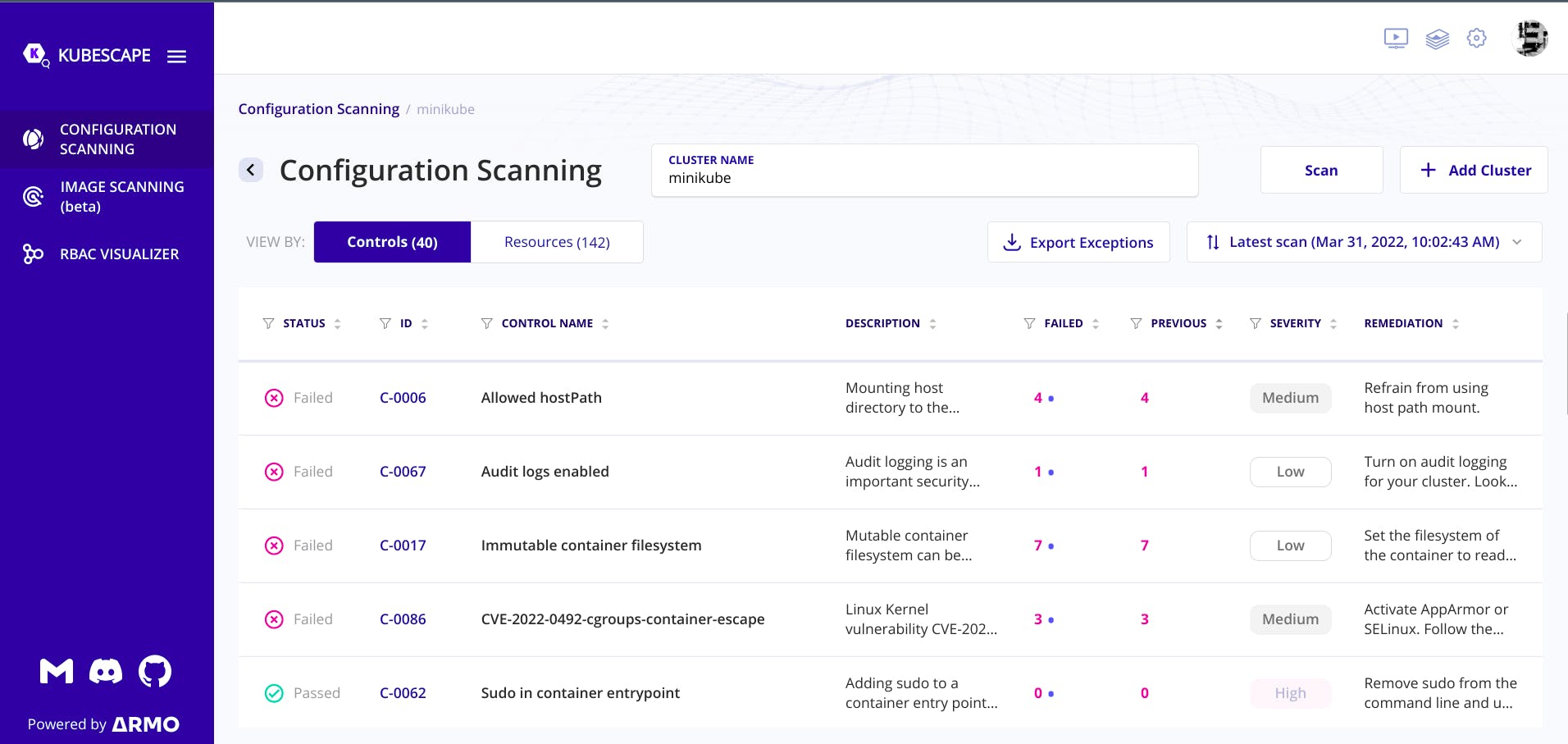
In the armo portal.
You can view the description of the errors by clicking the errors.
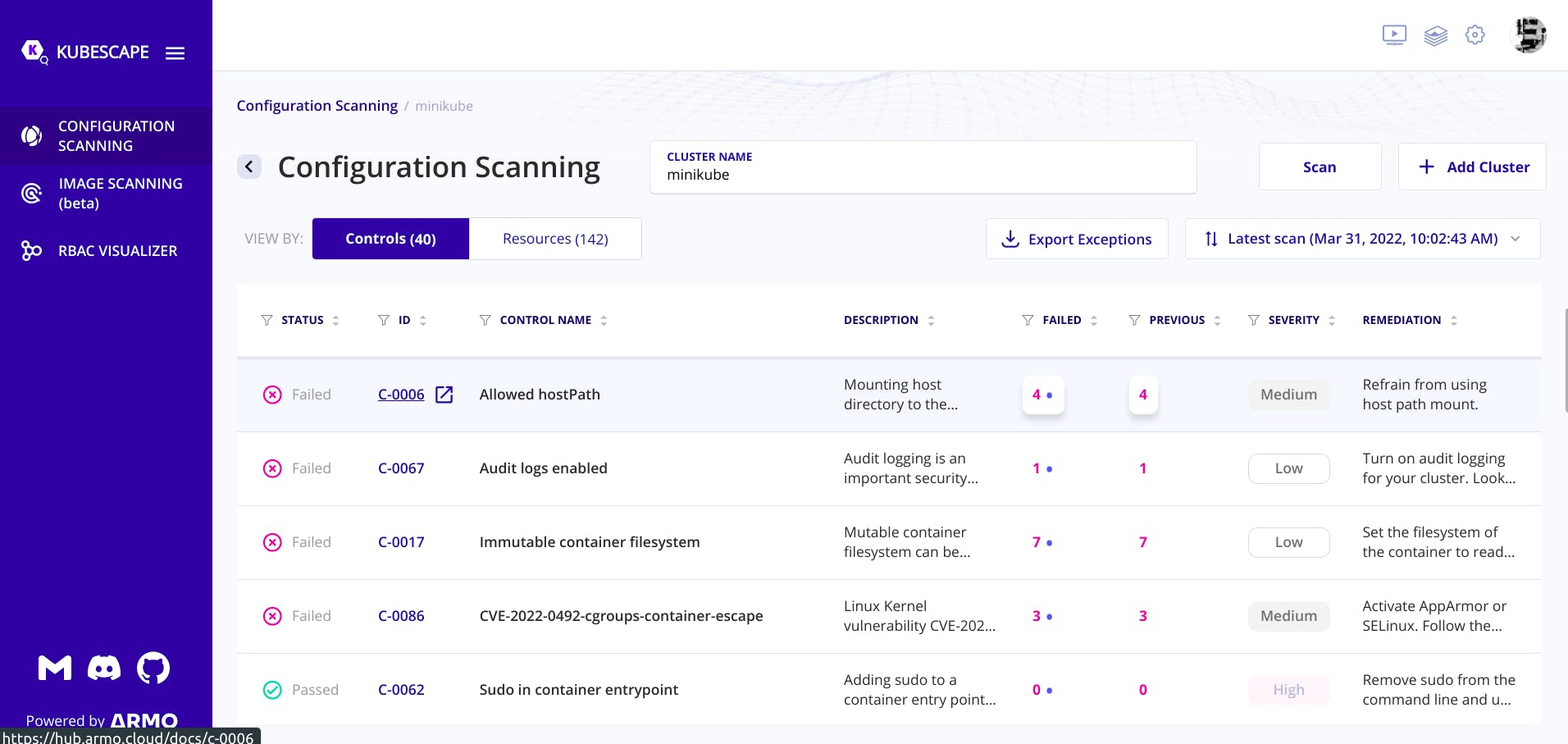
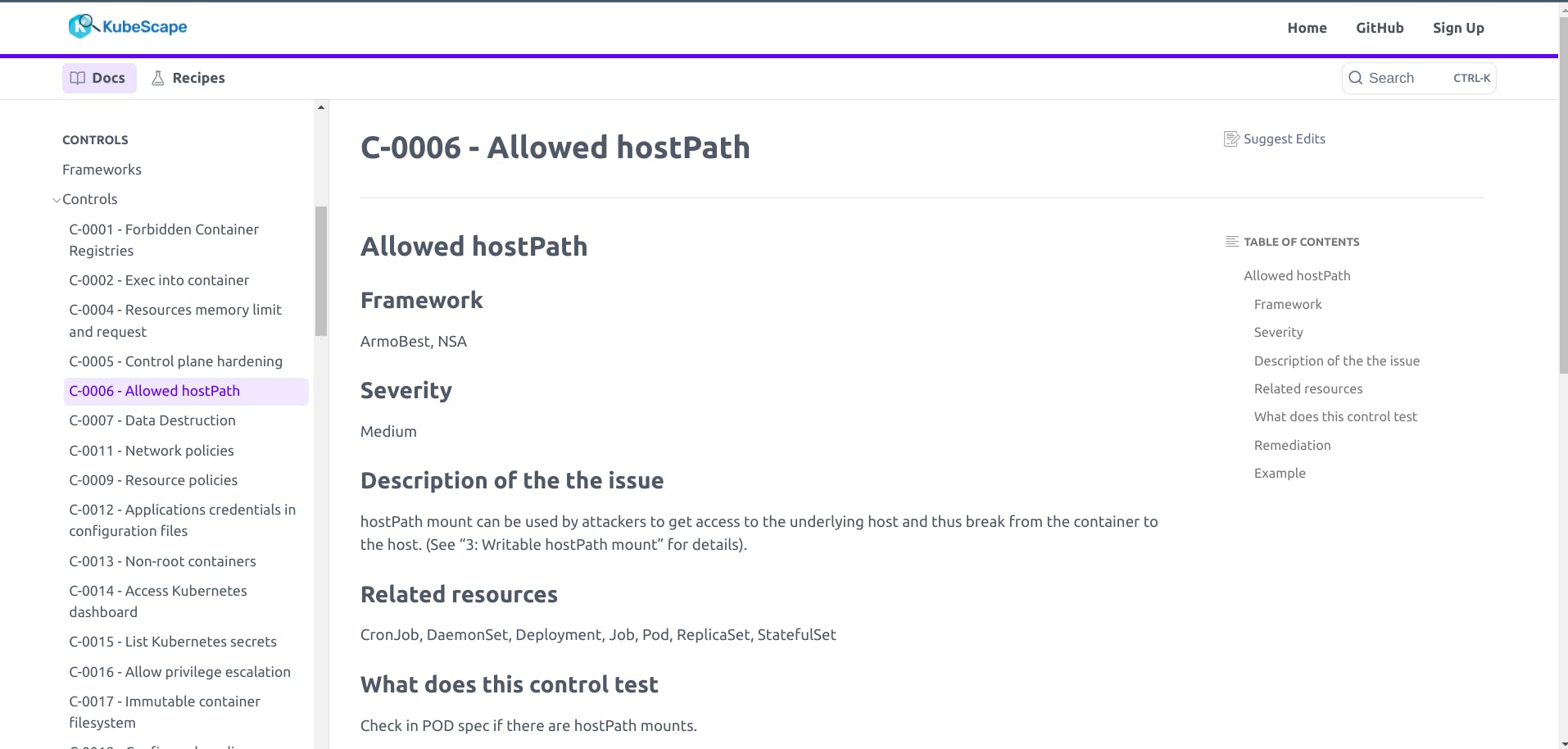
What we can see here, Framework represents who has created the framework, you can also create your own framwork and test it against your cluster.
Severity represents the severeness of the issue.
Rest of the things Description of the the issue, Related resources, What does this control test, Remediation can be easily understood and Example represents the yaml structure for it.
We can also the scores.
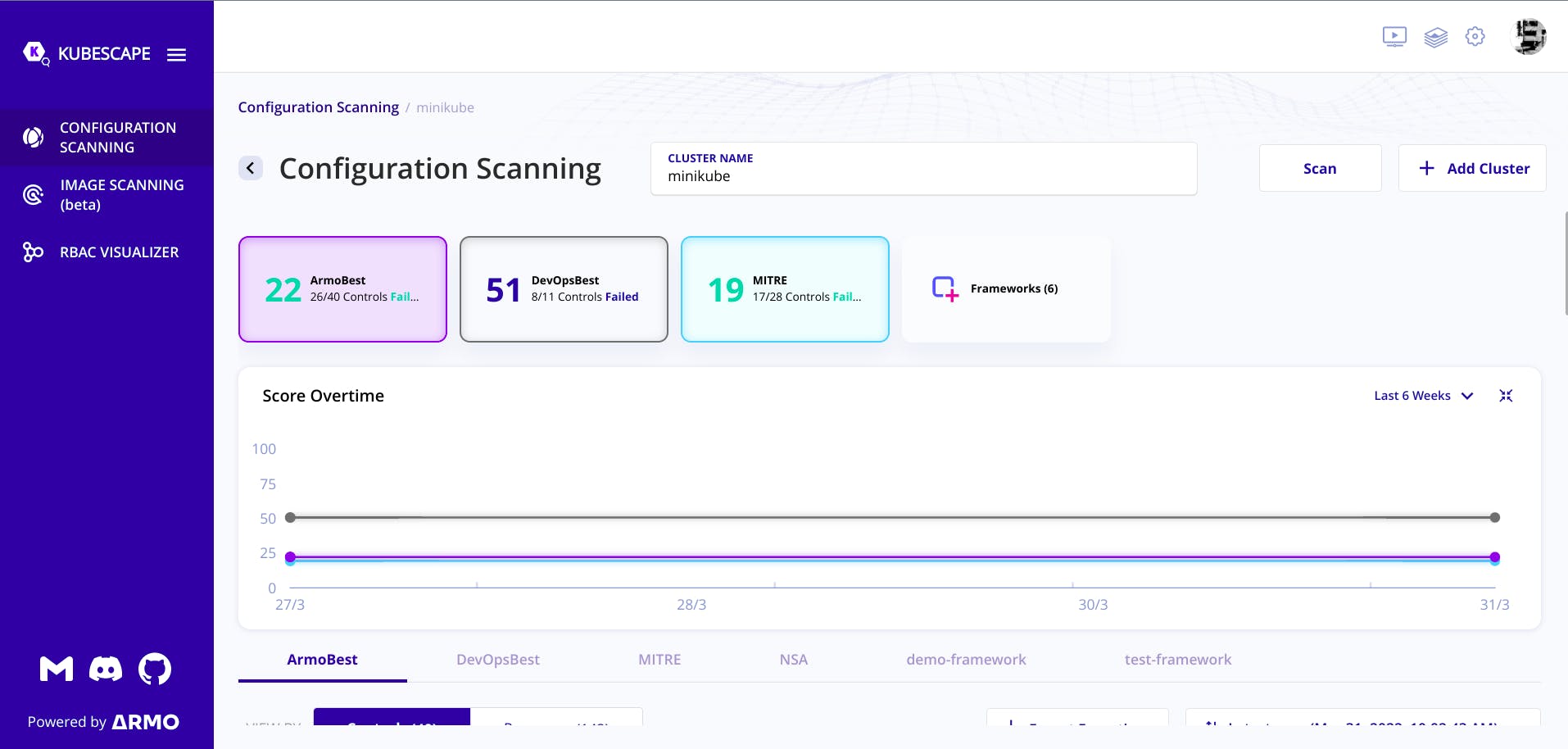
The ArmoBest score represents the armo site best scores, Devops Best score represents the Devops best scores around the world.
Creating custom framework for the cluster.
Framework > customize your framework
Give any framework name and tick the check box issue which you want to check against your cluster and save it you will see in the framwork tab in the home.
In my case I have created a test-framwork as framework.
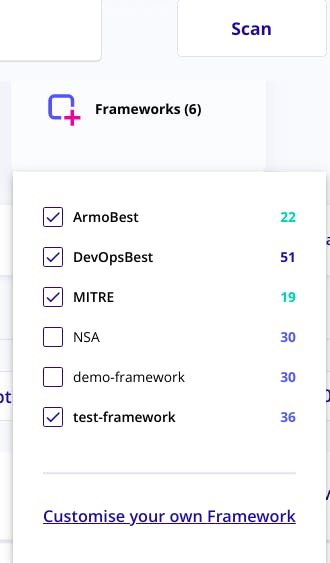
Now running the test with the new framework. Click your custom framework from the top which you just created.
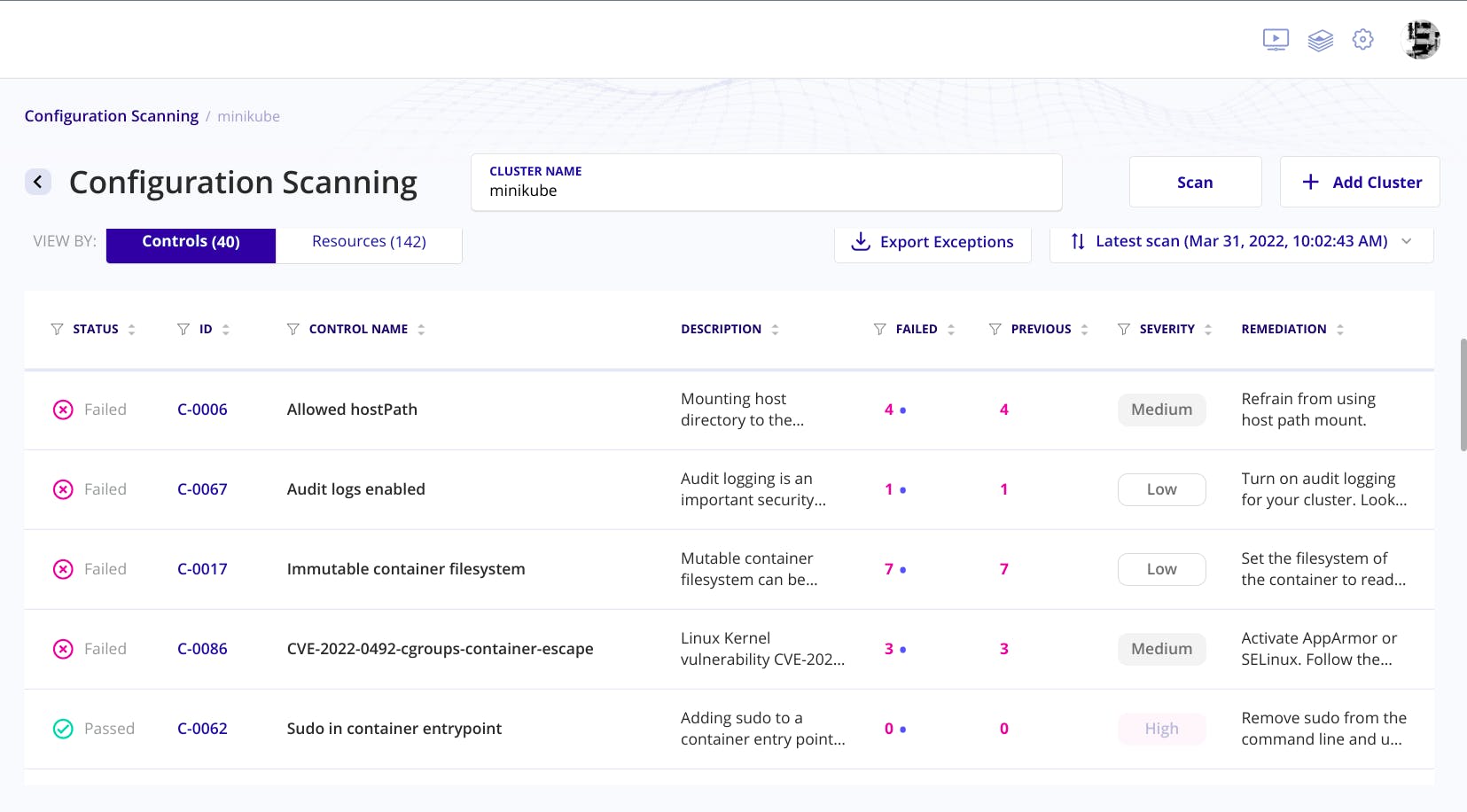
Rest of the things
Rbac visualizer represents the rbac configurations of the cluster in the arrow form.
Image scanning checks the image vulnerabilities.
Personal Abstract
I found the Kubescape very useful regarding kubernetes security as it checks the vulnerabilities in a cluster which is very important from an organization perspective. By reducing the manpower of checking everytime the vulnerabilities with bare eyes which is time consuming too. Kubescape makes it easier by allowing user to check the vulnerabilities and even ways to solve it. The GUI is the thing that creates the differentiation factor. Also, securing the k8's cluster is the major issue as it may lead to the leakage of the organization data and secrets. The custom framwork helps in creates the customized framwork according to the user/organization. The tools that has been used here is for easiness of this blog however you may use other tools as well.
Have anything to add?
Leave a comment down below. I'ld love to hear from you!!
And feel free to DM me on Twitter: iamyuvi
Thnks for reading and sharing!
